In this article, we’re going to configure a point-to-point IKEv2 Static Virtual Interface (S-VTI) between two Cisco CSR1000v routers using pre-shared keys as the authentication method.
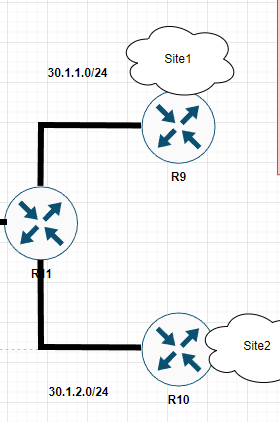
To demonstrate this, we’re going to use part of my lab topology as shown below.

R9 and R10 will be used to configure IKEv2 S-VTI.
Interface G1 on both routers will be used as the Internet-facing interface and we have Loopbacks configured for testing interesting traffic.
We can do this in 5 to 6 easy steps as shown below:
- Configure a keyring
- (Optional) Configure the IKEv2 Proposal
- Configure the IKEv2 Profile
- Configure the IPsec Profile
- Configure the Tunnel Interface
- Configure the static routes for interesting traffic
R9 IKEv2 S-VTI Configuration
1. CONFIGURE KEYRING
crypto ikev2 keyring IKEV2-KEYRING
peer R10
address 30.1.2.2 255.255.255.0
pre-shared-key local cisco
pre-shared-key remote cisco1
2. (OPTIONAL) CONFIGURE IKEV2 PROPOSAL
crypto ikev2 proposal default
encryption aes-cbc-256
integrity sha256
group 16
3. CONFIGURE IKEV2 PROFILE
crypto ikev2 profile IKEV2-PROFILE
match identity remote address 30.1.2.2 255.255.255.0
identity local address 30.1.1.2
authentication remote pre-share
authentication local pre-share
keyring local IKEV2-KEYRING
4. CONFIGURE IPSEC PROFILE
crypto ipsec profile IPSEC-PROFILE
set ikev2-profile IKEV2-PROFILE
5. CONFIGURE TUNNEL INTERFACE
interface Tunnel0
ip unnumbered GigabitEthernet1
tunnel source GigabitEthernet1
tunnel mode ipsec ipv4
tunnel destination 30.1.2.2
tunnel path-mtu-discovery
tunnel protection ipsec profile IPSEC-PROFILE
6. CONFIGURE STATIC ROUTE FOR INTERESTING TRAFFIC
ip route 40.0.1.0 255.255.255.0 tun0
R10 IKEv2 S-VTI Configuration
1. CONFIGURE KEYRING
crypto ikev2 keyring IKEV2-KEYRING
peer R9
address 30.1.1.2 255.255.255.0
pre-shared-key local cisco1
pre-shared-key remote cisco
2. (OPTIONAL) CONFIGURE IKEV2 PROPOSAL
crypto ikev2 proposal default
encryption aes-cbc-256
integrity sha256
group 16
3. CONFIGURE IKEV2 PROFILE
crypto ikev2 profile IKEV2-PROFILE
match identity remote address 30.1.1.2 255.255.255.0
identity local address 30.1.2.2
authentication remote pre-share
authentication local pre-share
keyring local IKEV2-KEYRING
4. CONFIGURE IPSEC PROFILE
crypto ipsec profile IPSEC-PROFILE
set ikev2-profile IKEV2-PROFILE
5. CONFIGURE TUNNEL INTERFACE
interface Tunnel0
ip unnumbered GigabitEthernet1
tunnel source GigabitEthernet1
tunnel mode ipsec ipv4
tunnel destination 30.1.1.2
tunnel path-mtu-discovery
tunnel protection ipsec profile IPSEC-PROFILE
6. CONFIGURE STATIC ROUTE FOR INTERESTING TRAFFIC
ip route 40.0.2.0 255.255.255.0 tun0
R9 Verification Check
R9(config)#do show ip int br
Interface IP-Address OK? Method Status Protocol
GigabitEthernet1 30.1.1.2 YES NVRAM up up
Loopback0 40.1.1.1 YES manual up up
Tunnel0 30.1.1.2 YES TFTP up up
R9(config)#do ping 40.1.2.1 source lo0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 40.1.2.1, timeout is 2 seconds:
Packet sent with a source address of 40.1.1.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/2 ms
R9(config)#do show crypto ikev2 sa
IPv4 Crypto IKEv2 SA
Tunnel-id Local Remote fvrf/ivrf Status
1 30.1.1.2/500 30.1.2.2/500 none/none READY
Encr: AES-CBC, keysize: 256, PRF: SHA256, Hash: SHA256, DH Grp:16, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/81650 sec
R9(config)#do show crypto ipsec sa
interface: Tunnel0
Crypto map tag: Tunnel0-head-0, local addr 30.1.1.2
protected vrf: (none)
local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
remote ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
current_peer 30.1.2.2 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 11295, #pkts encrypt: 11295, #pkts digest: 11295
#pkts decaps: 11311, #pkts decrypt: 11311, #pkts verify: 11311
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 30.1.1.2, remote crypto endpt.: 30.1.2.2
plaintext mtu 1438, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet1
current outbound spi: 0x471DC508(1193133320)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0xDD09F956(3708418390)
transform: esp-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2666, flow_id: CSR:666, sibling_flags FFFFFFFF80000048, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4607998/3540)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x471DC508(1193133320)
transform: esp-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2665, flow_id: CSR:665, sibling_flags FFFFFFFF80000048, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4607999/3540)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
R10 Verification Check
R10(config)#do show ip int br
Interface IP-Address OK? Method Status Protocol
GigabitEthernet1 30.1.2.2 YES NVRAM up up
Loopback0 40.1.2.1 YES manual up up
Tunnel0 30.1.2.2 YES TFTP up up
R10(config)#do ping 40.1.1.1 source lo0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 40.1.1.1, timeout is 2 seconds:
Packet sent with a source address of 40.1.2.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/2 ms
R10(config)#do show crypto ikev2 sa
IPv4 Crypto IKEv2 SA
Tunnel-id Local Remote fvrf/ivrf Status
1 30.1.2.2/500 30.1.1.2/500 none/none READY
Encr: AES-CBC, keysize: 256, PRF: SHA256, Hash: SHA256, DH Grp:16, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/81885 sec
R10(config)#do show crypto ipsec sa
interface: Tunnel0
Crypto map tag: Tunnel0-head-0, local addr 30.1.2.2
protected vrf: (none)
local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
remote ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
current_peer 30.1.1.2 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 6418, #pkts encrypt: 6418, #pkts digest: 6418
#pkts decaps: 6412, #pkts decrypt: 6412, #pkts verify: 6412
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 30.1.2.2, remote crypto endpt.: 30.1.1.2
plaintext mtu 1438, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet1
current outbound spi: 0xDD09F956(3708418390)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0x471DC508(1193133320)
transform: esp-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2731, flow_id: CSR:731, sibling_flags FFFFFFFF80000048, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4607993/3327)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0xDD09F956(3708418390)
transform: esp-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2732, flow_id: CSR:732, sibling_flags FFFFFFFF80000048, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4607996/3327)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)






Leave a Reply