YOUR CART
- No products in the cart.
Subtotal:
£0.00
BEST SELLING PRODUCTS

To accompany the recent vodcast, I am sharing the resources that I used to pass my CISSP. To understand how I used each of the resources below, please listen to the following vodcast. CISSP Resources I hope that helps – good luck and feel free to share your progress in…

Documentation types listed in order of most importance: Policy Examples of security policies: Acceptable Use Policy (AUP) or Bring Your Own Device (BYOD) Policy Standards Baselines Guidelines Procedures In an effort to help one remember the order of the aforementioned documents, the image I have created below represents each document…
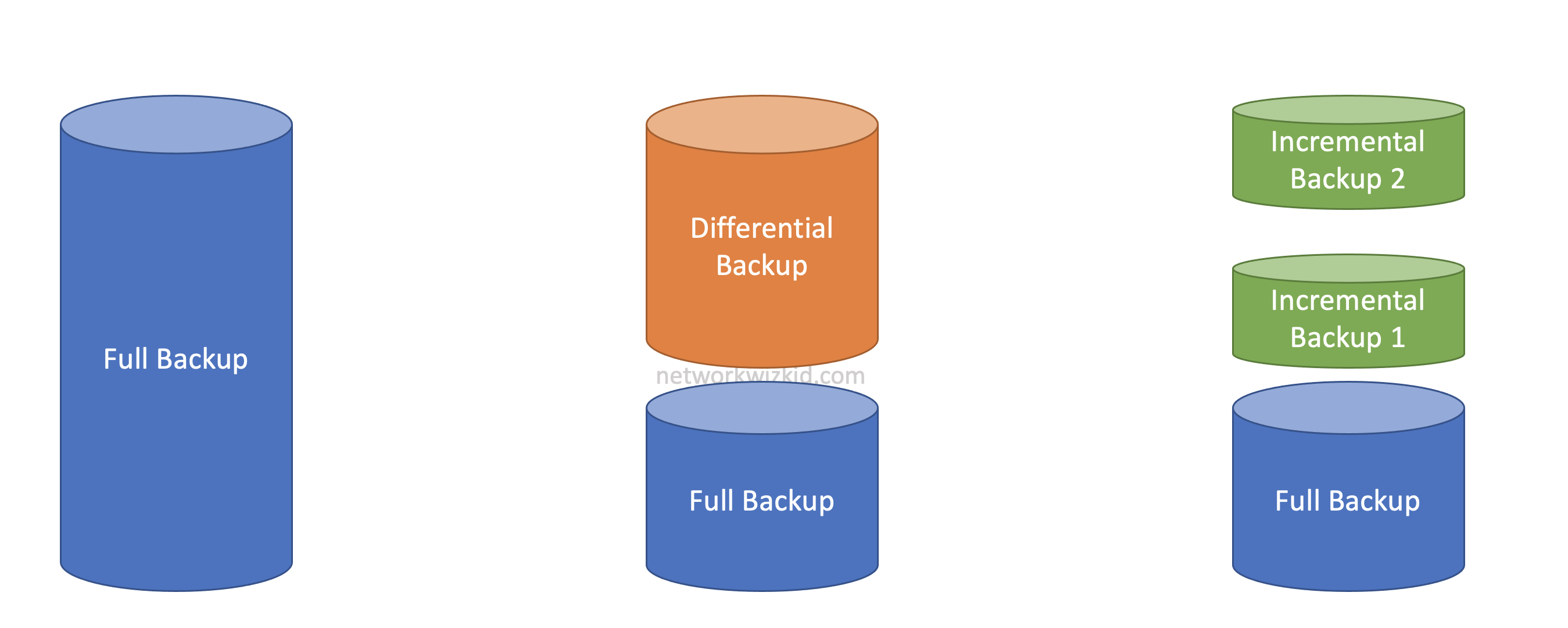
Full Backups Differential Backups Differential Backup Example Network Wizkid Corp performs a full backup of their servers every Sunday at 1:00 AM followed by differential backups at the same time every other day. If their server fails on Wednesday and requires restoration at 12:00 PM, Network Wizkid Corp will be…

Change Log Log Date Added cost/benefit analysis example updates and also added a cost/benefit analysis exercise 17/04/23 Added definitions for ‘safeguards’ and ‘countermeasures’ and included links for reference 17/04/23 Added more examples 12/05/23 When we talk about Risk Management, it’s important that we understand what Quantitative Risk Analysis is and…

Many people have reached out to me and asked where they can find the exam code for the ISC2 Certified in Cybersecurity (CC) certification. ISC2 haven’t made it very clear where those looking at getting a free shot at this certification can find the exam code and so I thought…

In this video, I discuss the resources used that helped me pass the ICS2 Certified in Cybersecurity certification and we take a look at what you need to give yourself the best chance of getting certified.