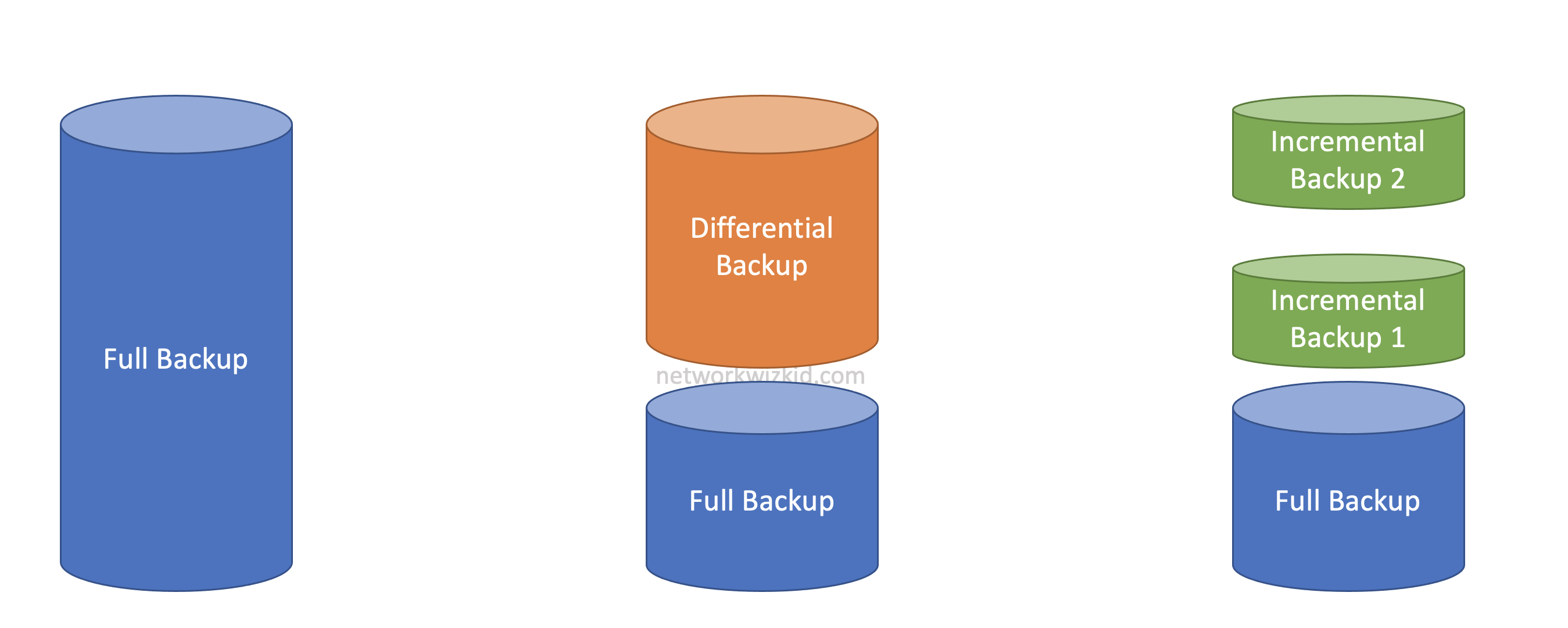
Full Backups
- A full data backup of all the data from a device
- Archive bit changed from 1 to 0 once the data has been backed up
Differential Backups
- A backup of files that have changed since the last full backup
- Only files with the archive bit set to 1 will be backed up
- Differential backups do not reset the archive bit to 0
- Differential backup are quicker to restore
Differential Backup Example
Network Wizkid Corp performs a full backup of their servers every Sunday at 1:00 AM followed by differential backups at the same time every other day. If their server fails on Wednesday and requires restoration at 12:00 PM, Network Wizkid Corp will be required to restore from the last full backup and the last differential backup only (Total of 2 backups = ((Differential Backup) Wednesday)) + ((Full Backup) Sunday)).
Incremental Backups
- A backup of files that have changed since the last full full backup OR since the last incremental backup
- Only files with the archive bit set to 1 will be backed up
- Archive bit changed from 1 to 0 once the backup is complete
- Incremental backup are longer to restore
Incremental Backup Example
Network Wizkid Corp performs a full backup of their servers every Sunday at 1:00 AM followed by incremental backups at the same time every other day. If their server fails on Wednesday and requires restoration at 12:00 PM, Network Wizkid Corp will be required to restore from the last full backup and the last three incremental backups (Total of 4 backups = ((Incremental Backups) Monday, Tuesday, Wednesday) + ((Full Backup) Sunday)).







Leave a Reply